- Published on
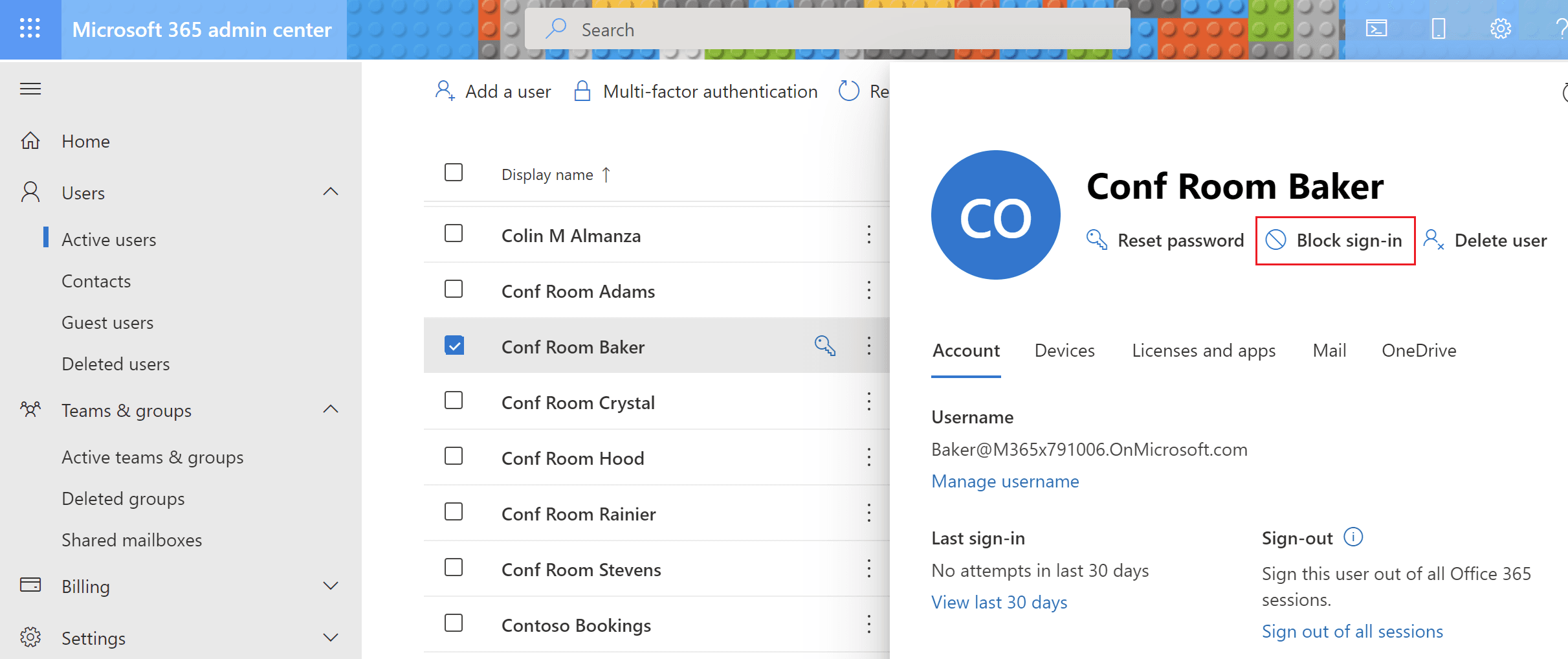
Securing Shared mailboxes to prevent sign-ins
- Authors
- Name
- Jonathan Devere-Ellery
When creating a new Shared Mailbox in Exchange Online it will automatically create an account in Azure AD in the background using a randomly generated password. Even though the initial password is unknown, it can be easily reset back to a known value, and then the account can be logged into as normal.
There is really no need to leave the account enabled for normal functionality of a Shared mailbox, so we should disable the accounts to prevent opportunities for abuse.
To disable these accounts using PowerShell, instead of using either the AzureAD and MSOL modules which are on the path to deprecation instead we will use the Microsoft Graph module to achieve it.
Install-Module Microsoft.Graph -Scope CurrentUser
Install-Module ExchangeOnlineManagement
Connect-ExchangeOnline
Connect-MgGraph -Scopes "User.ReadWrite.All"
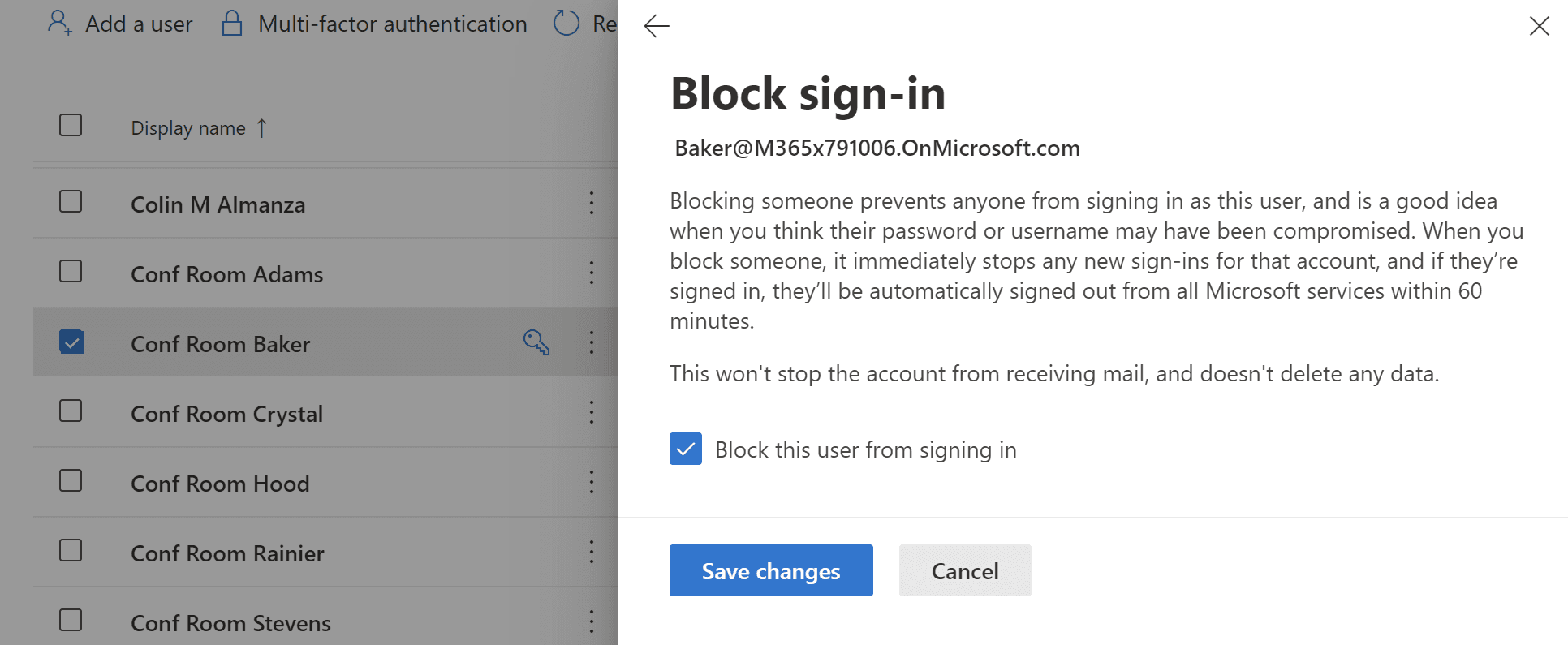
After we have connected, we can block credential sign-ins for a single mailbox simply by running:
$UserID = (Get-EXOMailbox "Conf Room Stevens").ExternalDirectoryObjectId
Update-Mguser -UserId $UserID -AccountEnabled:$false
Once we have tested this out and we're ready to disable all of the remaining Shared mailboxes in the environment we can easily scale this up. First we'll get a list of all the current Shared mailboxes along with the current state of the accounts, including the current values of AccountEnabled by running:
Get-EXOMailbox -RecipientTypeDetails "SharedMailbox","RoomMailbox","EquipmentMailbox" | ForEach {Get-MgUser -UserId $_.ExternalDirectoryObjectId -Property "AccountEnabled,DisplayName,Mail" | Select AccountEnabled,DisplayName,Mail}
Finally, to actually disable the Azure AD accounts for all Shared mailboxes, we can achieve it in a single command:
Get-EXOMailbox -RecipientTypeDetails "SharedMailbox","RoomMailbox","EquipmentMailbox" | ForEach {Update-Mguser -UserId $_.ExternalDirectoryObjectId -AccountEnabled:$false}
If we attempt to login with this account we will receive an error message, and it will appear in the AzureAD sign-in logs with a Sign-in error code of 50057 indicating that the user account is disabled: